Tag Cloud
Currently Reading
Latest Book Reviews
- Certified Kubernetes Application Developer (CKAD) Study Guide, 2nd Edition Posted on January 11, 2025
- Rancher Deep Dive Posted on March 31, 2023
- Leveraging Kustomize for Kubernetes Manifests Posted on March 24, 2023
- Automating Workflows with GitHub Actions Posted on October 13, 2022
- Deep-Dive Terraform on Azure Posted on August 30, 2022 All Book Reviews
Latest Posts
- Monitoring DHCP server with check_dhcp Posted on February 5, 2013
- Custom WordPress auto update via FTP Posted on January 20, 2013
- Certificate validation issue during Spacewalk install Posted on January 20, 2013
- OpenBSD: PF firewall for the paranoid Posted on January 13, 2013
- Writing custom Nagios plugins: check_public-ip Posted on January 2, 2013
February 5, 2013
Monitoring DHCP server with check_dhcp
by Alpha01
Setting Nagios to monitor my DHCP server using the plugin check_dhcp was a little tricky to setup.
First, the check_dhcp documentation indicates setting setuid on the check_dhcp binary in order to successfully query the dhcp server and receive a valid dhcp offer.
Error
root@monitor libexec]# su - nagios -c '/usr/local/nagios/libexec/check_dhcp -s 192.168.1.2'
Warning: This plugin must be either run as root or setuid root.
To run as root, you can use a tool like sudo.
To set the setuid permissions, use the command:
chmod u+s yourpluginfile
Error: Could not bind socket to interface eth0. Check your privileges...
Fix
chown root.root check_dhcp
chmod u+s check_dhcp
Secondly, since I always have all of my machines block all incoming traffic, I had to open up the UDP Port 68 in order for the Nagios machine to accept the dhcp offer.
iptables -A INPUT -p udp --dport 68 -j ACCEPT
networking nagios iptables January 20, 2013
Custom WordPress auto update via FTP
by Alpha01
When I originally migrated my blog off GoDaddy, one of the things that stopped functioning was the WordPress auto update feature. Luckily, I was able to easily overcome this using my own custom FTP settings. For its simplicity, I used vsftpd.
Install:
yum install vsftpd
chkconfig vsftpd on
Configure vsftpd to jail FTP users to their home directory in /etc/vsftpd/vsftpd.conf:
chroot_local_user=YES
Restart vftpd:
/etc/init.d/vsftpd restart
Now, I’ll create the user that will be used to download and install the WordPress auto updates:
useradd -d /PATH/TO/WORDPRESS/SITE -G apache -s /sbin/nologin apache_ftp_user
passwd apache_ftp_user
Before applying an update, update your permissions:
chown -R apache_ftp_user:apache /PATH/TO/WORDPRESS/SITE
Now use apache_ftp_user username and password on the WordPress FTP connection wizard page:
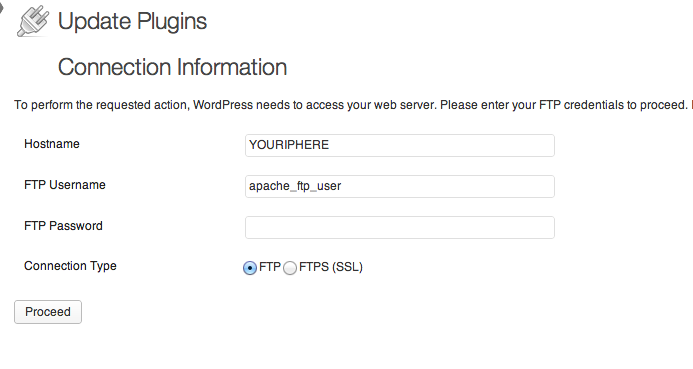
wordpress January 20, 2013
Certificate validation issue during Spacewalk install
by Alpha01
Error
For some really annoying reason Spacewalk failed to populate the database during the initial setup.
[root@spacewalk ~]# spacewalk-setup --disconnected --external-db
** Database: Setting up database connection for PostgreSQL backend.
Hostname (leave empty for local)?
Database? dbnamehere
Username? usernamehere
Password?
** Database: Populating database.
The Database has schema. Would you like to clear the database [Y]? Y
** Database: Clearing database.
** Database: Shutting down spacewalk services that may be using DB.
** Database: Services stopped. Clearing DB.
** Database: Re-populating database.
*** Progress: ##################################
* Setting up users and groups.
** GPG: Initializing GPG and importing key.
* Performing initial configuration.
* Activating Spacewalk.
** Loading Spacewalk Certificate.
** Verifying certificate locally.
** Activating Spacewalk.
There was a problem validating the satellite certificate: 1
Fix
Make sure your user’s database password does not have special characters!
Tags: [centos January 13, 2013
OpenBSD: PF firewall for the paranoid
by Alpha01
Block all traffic except for ssh.
/etc/pf.conf
tcp_services = "{ 22 }"
block all
pass out on em0 proto tcp to any port $tcp_services keep state
pass in on em0 proto tcp to any port $tcp_services keep state
Enabling rules:
pfctl -e ; pfctl -f /etc/pf.conf
pfctl: pf already enabled
pf January 2, 2013
Writing custom Nagios plugins: check_public-ip
by Alpha01
Now that I think Nagios is the greatest thing since slice bread, I’m slowly but surely re-writing all my custom monitoring scripts to Nagios plugins.
The following is a Nagios plugin ready script that I used to replace my old public IP monitoring (See https://www.rubysecurity.org/ip_monitoring).
#!/bin/bash
STATE_OK=0
STATE_WARNING=1
STATE_CRITICAL=2
STATE_UNKNOWN=3
current_ip="YOUR-IP-ADDRESS-HERE"
ip=`curl -connect-timeout 30 -s ifconfig.me`
if [ "$current_ip" != "$ip" ] || [ -z "$ip" ]
then
if [[ "$ip" =~ "Service Unavailable" ]] || [[ "$ip" =~ "html" ]]
then
echo "IP service monitoring is unavailable."
exit $STATE_WARNING
elif [[ "$ip" =~ [0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3} ]]
then
echo "ALERT: Public IP has changed. NEW IP: $ip"
exit $STATE_CRITICAL
else
echo "Unknown state detected."
exit $STATE_UNKNOWN
fi
else
echo "Public OK: $ip"
exit $STATE_OK
fi
bash nagios 